Secure IoT: P2P SSH Connections Explained
In an era defined by unprecedented technological advancements, is it truly possible to guarantee the safety of our interconnected devices and networks? Securing remote IoT devices through peer-to-peer (P2P) SSH connections has evolved from a best practice to an absolute necessity, especially in the face of increasingly sophisticated cyber threats. The relentless ingenuity of malicious actors demands a proactive and robust approach to cybersecurity, and P2P SSH offers a vital layer of defense.
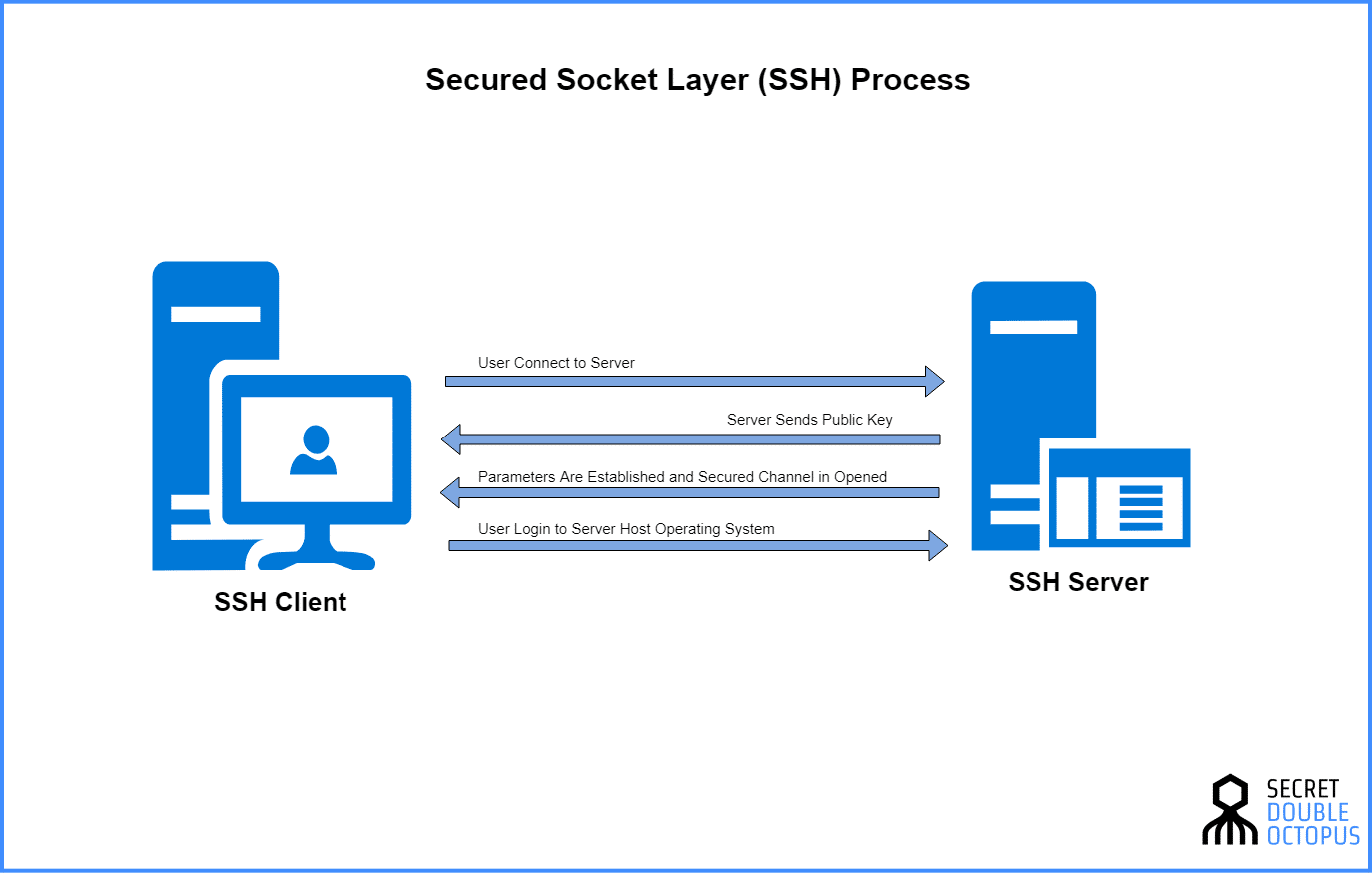
Setting up SSH, while a fundamental step, is merely the beginning. The true challenge lies in establishing secure connections with your remote IoT devices, a task made complex by firewalls, network configurations, and the constant threat of interception. However, by leveraging P2P SSH, we can establish direct, encrypted pathways to these devices, allowing for secure management and control from virtually anywhere in the world. This method not only protects our resources but also significantly bolsters the overall security posture of the entire system. The inherent encryption within the SSH tunnel is a cornerstone of this protection, ensuring that all data traversing the network is rendered unreadable to unauthorized parties, including the service providers themselves.
Let us delve into the specifics of P2P SSH, exploring the tools and techniques that empower us to establish and maintain these vital connections. The landscape of remote device management is diverse, and the tools available reflect this diversity. From open-source solutions to proprietary platforms, the choices are numerous. However, the fundamental principles remain consistent: secure, encrypted communication is paramount. The beauty of a well-configured P2P SSH setup lies in its ability to bypass the limitations imposed by traditional network architectures. Devices behind firewalls, often the most vulnerable, become accessible without complex port forwarding or network address translation (NAT) configurations. This streamlined approach simplifies management and reduces the attack surface, thereby minimizing potential vulnerabilities.
- All About June 21st Birthstone Meaning History And Benefits
- Secrets Of Undefined Curly Hair Tips Care And Styling
One particular platform, "Remoteiot," exemplifies the potential of this approach. Designed to facilitate secure connections to machines and devices from any location, Remoteiot leverages the power of P2P SSH to provide a robust and user-friendly solution. The platforms core feature is the ability to establish encrypted tunnels that keep data safe from prying eyes, ensuring that all network traffic is protected during transit. Such features offer a critical advantage in the ongoing battle against cyber threats. With the right approach, you can connect to devices located anywhere in the world, protected by strong encryption and security protocols.
Windows 10's native OpenSSH capabilities offer a convenient and readily available solution for establishing secure, direct connections. With OpenSSH pre-installed, users can avoid the need for third-party software and quickly implement P2P SSH connections on their systems. This built-in functionality provides everything needed to securely access and manage remote devices. However, the deployment of this approach across a diverse range of devices requires careful consideration of the device-specific configurations. Specifically, the Raspberry Pi, renowned for its versatility in IoT applications, is frequently a target for such connections. Setting up a Raspberry Pi for remote access involves several key steps, from initial configuration to SSH key management and firewall adjustments, all of which must be implemented precisely.
The following table provides a detailed overview of the key components and considerations for securely connecting remote IoT devices via P2P SSH:
- Effective Remedies And Causes Of Dark Armpit Skin
- Astrology For Couples Enhance Your Relationship With The Stars
| Component | Description | Importance |
|---|---|---|
| SSH (Secure Shell) | A cryptographic network protocol for secure operations over an unsecured network. It provides a secure channel over an unsecured network in a client-server architecture, connecting to a server host. | Provides the foundation for secure communication, authentication, and data transfer. |
| P2P (Peer-to-Peer) | A decentralized network architecture where devices (peers) communicate directly with each other. | Eliminates the need for a central server, offering flexibility and improved security. |
| Encryption | The process of converting data into a coded form to prevent unauthorized access. Commonly employed encryption algorithms include AES and RSA. | Protects data in transit, ensuring confidentiality and integrity. All data is encrypted within the SSH tunnel. |
| Firewall Configuration | Setting up rules to control network traffic to and from a device. This includes allowing SSH traffic on the relevant port (usually port 22) and configuring rules to restrict access to authorized IP addresses only. | Prevents unauthorized access to the device and minimizes the attack surface. |
| Key-Based Authentication | Utilizing cryptographic keys for authentication, rather than passwords. This improves security. Public-key authentication involves creating a key pair (a private key, which is secret and kept secure, and a public key, which can be shared.) | Enhances security and simplifies the login process by eliminating the need for password entry. This is a critical step in securing remote access to IoT devices. |
| Port Forwarding/NAT Traversal (if needed) | Techniques used to allow access to devices behind a NAT firewall or router. This involves configuring the router to forward traffic on a specific port to the internal device. | Enables secure connections to devices located behind firewalls or NAT routers. (However, P2P often circumvents the need for this). |
| Remoteiot (Example Platform) | A platform designed to facilitate secure connections to machines and devices from any location. | Simplifies the management of remote devices by offering an integrated solution for secure connections. |
| Raspberry Pi Configuration | The process of setting up a Raspberry Pi for remote access involves several key steps, from initial configuration to SSH key management and firewall adjustments. | Ensures that devices are properly configured for secure remote access. |
| Regular Security Audits | Regularly reviewing system configurations, logs, and security practices to identify and address vulnerabilities. | Maintains the ongoing security of the system and helps to mitigate the risk of attack. |
| Software Updates | Keeping all software, including the operating system, SSH server, and any related tools, up-to-date with the latest security patches. | Addresses known vulnerabilities and strengthens the overall security posture. |
The proliferation of IoT devices has created a vast network of interconnected systems, generating an unprecedented amount of data. This data, however, is vulnerable to malicious actors who may seek to exploit weaknesses in device security. As a result, securing these devices is not just about protecting individual components; it is about protecting the entire system. SSH provides a secure and reliable method for accessing and managing these devices. The P2P structure avoids a single point of failure and enhances the resilience of remote access.
The adoption of P2P SSH in the IoT landscape has also driven the evolution of supporting tools. Platforms, like Remoteiot, have risen to meet the evolving demands. These tools provide streamlined solutions for connecting, managing, and monitoring IoT devices, providing users with a central point of control.
The key is to ensure that only authorized individuals can access the devices and that all data transmitted between them is encrypted. This protection can prevent unauthorized access and data breaches. The integration of these technologies into an IoT infrastructure requires a strategic approach, where security is prioritized at every level, from the selection of devices to their ongoing maintenance. By adhering to the principles of secure connection and careful configuration, organizations can significantly mitigate the risks associated with remote access and maintain the integrity of their IoT systems.
Article Recommendations
- Perfecting Your Look Haircuts For A Heart Shaped Face
- Chic And Modern Womens Short Hairstyles Your Ultimate Guide


Detail Author:
- Name : Prof. Trent Parisian III
- Username : ojenkins
- Email : ohara.bryce@corwin.org
- Birthdate : 2007-02-04
- Address : 670 VonRueden Heights Suite 047 Zemlakshire, HI 80166
- Phone : 423.510.0381
- Company : Kirlin, Schinner and Funk
- Job : Legal Secretary
- Bio : Aliquid et perferendis optio. Voluptatem vitae officiis et ut voluptas. Dolorem atque quasi in rerum dignissimos non saepe.
Socials
facebook:
- url : https://facebook.com/waltere
- username : waltere
- bio : Qui consectetur placeat qui temporibus.
- followers : 2039
- following : 316
twitter:
- url : https://twitter.com/ericwalter
- username : ericwalter
- bio : Esse in voluptatem sunt reprehenderit. Et at officiis quasi. Aut fugit et ullam impedit.
- followers : 116
- following : 484
tiktok:
- url : https://tiktok.com/@eric3346
- username : eric3346
- bio : Et deleniti et et consectetur. Et animi velit impedit reprehenderit.
- followers : 2491
- following : 2236